Our preliminary quantitative and qualitative findings tally with other studies of the online workplace abuse of adults in a variety of professions (e.g. Doidge 2013; Williams et al. 2013). Phippen's (2011) report, commissioned by the UK Safer Internet Centre and concentrated upon teachers and other individuals working in education, employed a similar methodology to our own, grounded in an online questionnaire distributed to teachers via email lists, and supplemented by interviews and study of cases reported to the Professionals Online Safety Helpline. Herein, 35% of 377 survey respondents had encountered online abuse in their working lives, or witnessed colleagues experiencing such abuse. Moreover, Phippen's (2011) results parallel ours in demonstrating the migration of offline abuse behaviours into the online world (and the likelihood of target and abuser being known to one another offline), as well as in documenting the deep mental health tolls upon victims.
Cassidy et al.'s (in prep) pioneering enquiry into cyberbullying at four Canadian universities (based on data from more that 2,000 students and teaching staff), concluded that approximately 20% of students reported such bullying, while between 72-79% of teaching staff reported being 'extremely or somewhat concerned' by online bullying against themselves. Many staff documented cyberbullying by their own colleagues; women were victimised significantly more often than men; more than one in two teaching staff described a desire to quit as a consequence; and 20% of teachers at two of the universities reported suicidal feelings in relation to the abuse.
Lupton's (2014) international online survey of 711 academics echoes our findings of the complicated impacts of social media on higher education professionals. These include tangible benefits for research, networking and professional visibility, but also worrisome and potentially harmful consequences relating to loss of privacy, plagiarism, commercialisation and abuse, among other matters. Eckert's (2014) interview-based study of 109 female bloggers/online writers similarly notes that despite universal recognition among her research participants of the promises of web-based media, 3 in 4 had been subject to negative experiences (most commonly harassing comments), and 72% questioned the democratising capacities of these media.
In effectively all existing research, the lack of support for victims and the near total absence of rigorous mechanisms for reporting, prevention and punitive action are pronounced. As Eckert (2014) writes, 'Negative experiences were dealt with mostly on a personal level, as police, state and lawmakers have been slow in recognizing and prosecuting online discrimination and abuse levelled against women'. Disturbingly, Eckert's conclusions hark back to our own. Among our archaeology/heritage-specific survey respondents, only 59% (23 out of 39) reported taking some form of action in reply to their harassment - most of which was done independently, without support from external parties. Twenty-two of these respondents (95.7%) provided long-hand descriptions of their actions, which we coded into 12 categories.

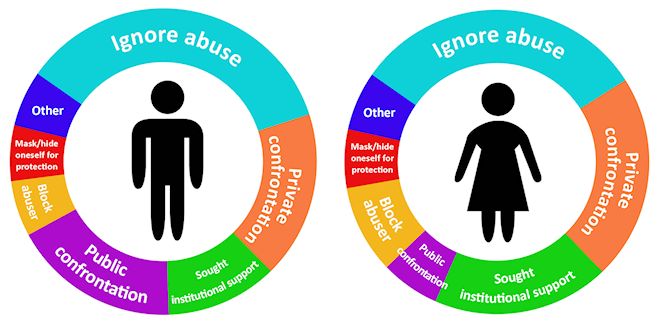
By far, the most common was to disregard the situation completely (16 instances), with various individuals specifically stating, for example, that they ignored it, seeing this as the most productive form of reply. Other actions (sometimes applied in combination with one another) included the respondent either privately calling out their abusers via telephone or in-person conversation (10 instances), or seeking institutional support to manage the predicament (8 instances), or personally calling out the abuser on a public forum or to other members of the public (5 instances), or blocking/unfollowing/banning/deleting evidence of the abuser (4 instances), or hiding/deleting/altering their own account to protect themselves (3 instances), among a handful of other unique responses (Figure 6).
Perhaps the most disturbing of all of these reports entailed cases where respondents sought institutional support, but received none in return. As Mark (41) puts it:
'I raised the matter in my office. At first with complaints that something need[ed] to be done. Unfortunately my manager is both busy and an old friend of the party involved. I had to ramp it up the ladder, several times. I checked with the union for support, but none was available! I finally threatened to take legal action on my own, advising my director that I was being defamed and harmed and that they were doing nothing to protect me.'
Paralleling our findings, Phippen's (2011) study of the teaching community found that more than 25% of those who reported abuse to their senior managers saw little or no meaningful response. Comparably, more than 50% of those who reported to their unions, and more than 60% who reported to the police, felt their respective interventions were ineffective or, indeed, actually worsened the situation. Faucher et al. (in press), in reference to their Canadian cyberbullying research, neatly summarise the regulatory situation as one wherein, for adults, there is seemingly 'less concern with the victim's rights, such as the right to security of person, than with the accused's rights, such as freedom of expression'. Marwick and Miller's (2014) scan of American legal remedies to online hate speech, harassment and defamation concluded that despite the significance of the problems, extant laws were primarily impotent, victims were 'rarely taken seriously' by law enforcement, and for the most part, 'the best victims can hope for is that, in unmasking the perpetrator, a loss of anonymity will be enough to stop online harassment'. Moreover, Marwick and Miller (2014, 5) note blatant structural divides, with women, and sexual and ethnic minorities reporting the highest magnitude of online abuse.
Of the handful of studies of workplace policies centred on managing such online interactions, findings confirm a lackadaisical, oftentimes aloof approach which regularly places the onus on the abused to resolve their own predicament or to change their own behaviour, or which is otherwise out-of-step with the current technological landscape. For instance, research by Faucher et al. (in press) and Jones and Scott (2012) into cyberbullying in university contexts establishes that the most common policies focus on student codes of conduct, with little sense that staff and others beyond the institution might be similarly affected by - or the causes of - such bullying, and with few disciplinary sanctions. Resolution here tends to revolve around educational efforts versus punishment, where the latter entail revoking access to technology at the university, as though this technology is not available elsewhere (e.g. on the perpetrators' personal mobile phones or tablets with external provider-based internet access). Prevention mechanisms were similarly rare in these contexts.
We conducted our own scan of protection and prevention policies related to online harassment in the UK university sector, searching for robust, coherent strategies that might be used as models of good practice across archaeological/heritage institutions. Given the knowledge exchange priorities and highly public nature of much current archaeology and heritage practice, higher education institutions (whose public visibility and knowledge exchange agendas are arguably comparable) seemed a likely source for relevant policy frameworks. We analysed ten such frameworks, gathered from the web in the public domain, and anonymously through supporters of our research who shared internal institutional documentation. Generally, each policy recommended a three-point victim-driven pattern of action that was mirrored in the actions of our survey respondents. This included encouraging subjects of abuse to confront their abusers personally, then (if such personal confrontation failed) to reach out to counsellors or informal mediators for advice and support, then (if such mediation failed) to make a formal complaint against the abuser (e.g. see the current policies of the University of Exeter, and University of Sheffield).
However, these recommendations place the burden on the victim, and often lack blatantly visible, simple, streamlined means to encourage reporting and follow-up. Moreover, at each stage of escalation they arguably place the victim at risk, since to confront an abuser could result in further abuse or intimidation, particularly if an imbalance of professional status exists between abuser and target. The second stage of mediation is impossible to enforce when the abuser is not employed by the same institution as the abused. This problem also afflicts the third stage of formal action, where little if any recourse is available to victims if they are not employed by the same place as their abuser. Only the University of Cardiff acknowledges this problem in their 'Anti-Social Media' policy, suggesting that it would attempt to 'locate the owner' of problematic content and ask them to remove it, but with no guarantee of protection and prevention in the future. Cardiff is also the only institution in the sample to provide a form for victims to download and submit - the single institution in our sample that easily facilitates reporting of abuse.
Speaking in confidence about their unpublished institutional strategies, multiple informants to our project highlighted what seems to be common practice. As one informant wrote of their university, 'we've got some really basic samples of netiquette guidelines but nothing more formal than that'. Another archaeologist noted that 'guidance on social media is that if the person doing the cyber-bullying is in no way connected to my institution, it is not the University's problem' (anonymised pers. comm. to Perry, October 2013). In the latter case, following Faucher et al.'s (in press) definitions of cyberbullying, the abuse is appreciated by the institution not as a violation of human rights, not as an instance of violence against a person (as it might be were it a physical as opposed to digital threat), and not even as a matter of incivility. Instead, it is simply nothing. Thus while our profession seems increasingly absorbed with making itself and its practitioners more public-facing (and, in some contexts, mandating such visibility), it apparently has virtually no attendant concern for how to grapple with the risks of this access.
The hypocrisy of such a predicament might imply that resolution and management mechanisms are non-existent or hopeless. However, there are various individuals and bodies who are committed today to articulating means to prevent, protect and penalise those whose online communications infringe upon others, and who seek to ensure that in our rush to adopt new digital modes of engagement we are not simply replicating existing structural divides (see Perry 2014). Kate Clancy (2013) is among those who have argued for cross-institutional codes of conduct - rather than one-off policies implemented and patrolled independently - a proposal that a professional body such as the Institute for Archaeologists would be well placed to develop. JISC Legal has ventured into this territory for the higher education sector with its social media policy template and checklist (2014a; 2014b), providing a blueprint for others to draw upon in crafting institutional e-safety and acceptable use guidelines. Clancy (2013) also calls for community response tools that allow people to join together in solidarity, flagging inappropriate content and exposing aggressors (e.g. via the #trollerderby hashtag on Twitter). Such an approach is easily implemented in archaeological forums such as conferences and participatory contexts where social media are in use, and where moderators of these media can be equipped in advance to detect, prevent and defuse problematic communications, and to act as highly-visible marshals for those affected by such communications.
A growing number of resources are available online to those seeking to cultivate e-safety as they embark upon projects, for instance Eckert's (2014) safe blogging guidelines. Such preventative efforts must be accompanied by protective approaches with proven impact in the offline world, including raising awareness of the prevalence of abuse and, in so doing, drawing attention to reporting mechanisms and channels for recognising and managing it (see Clancy et al. 2014). Where it does manifest, speaking accurately and in uncensored fashion about its nature (e.g. quoting the exact language used as opposed to paraphrasing via generalities) is critical to exposing its offensive tone, which as Jane (2014) notes, is often glossed over despite the fact that it causes harm, ostracises individuals, and would otherwise be considered unacceptable in the offline world. These actions align with aspects of Fuchs' (2014) strategy for cultivating a true participatory democracy on the social web, as opposed to the exploitative, corporate-controlled commodity that he argues it to be. By his reckoning, 'Action is always related to events. If there is no knowledge about oppressive practices because they are hidden from the public, then reactions to it are unlikely' (Fuchs 2014, 263). The extant data make obvious that such oppressive practices are now habitual in online communications - their prevalence is not in doubt - which means that protective mechanisms are not luxuries, but incontestable necessities that those who demand engagement with the social web have a duty of care to supply to their contributors.
Moreover, as Clancy et al. (2014, 8) chronicle, 'Supervisors are the primary determinants of workplace culture. Therefore, principal investigators have the greatest power and responsibility to steward field sites that foster worker wellbeing and thus promote productivity and retention of [staff]'. Extrapolating from their offline-focused findings, this means that supervisory-level professionals have an obligation to model good practice, intervene where questionable behaviour manifests itself, speak candidly about the very real potential for abuse, set in place acceptable use and e-safety policies, and nurture a culture of respect and, at once, non-tolerance for disrespect of such customs.
As we have noted elsewhere (Perry 2014), we are now at a watershed moment where the risks of online communication are irrefutable and the current apathetic - or potentially even wilfully naive - system within the heritage industry is unsustainable. The discipline and its various backers have no excuse to continue investing in campaigns that are ostensibly focused on inclusivity and impact, but which, in reality, have no consciousness of - or means to safely negotiate - the fallout of such impact, nor any capacity to cultivate true inclusion. Such seems to be the normal state of affairs in the heritage sector where, as Richardson (2014, 289, 291) documents, organisations have little relevant strategic planning at the ready, their social media presences are regularly outsourced to a few volunteers, and their participatory media practices do not tend to actually produce inclusive dialogue nor a diversity of alternative narratives (also see Walker 2014). To borrow Richardson's (2014, 289) language, this predicament is precarious, transient and poorly supported, breeding unsustainability, imbalances of power and, ultimately, exclusivity. We would suggest, in fact, that it is not only deeply contradictory, but fundamentally unethical. Those institutions (whether front-line deliverers of heritage, universities, funding bodies or other sponsors) who mandate such online engagement without robust planning, protection, prevention and punitive mechanisms in place are culpable of breaching their duty of care.
As professionals or professionals-in-training, we too have a responsibility to call out and aim to avoid supporting and investing in projects with ill-conceived, superficial, unmonitored, unaccountable online media practices. Otherwise we risk replicating a system that produces exactly the opposite of the democratising, empowering, progressive engagement such social media are intended to achieve.
We would like to invite readers to contribute anonymously to a Google document detailing their thoughts on how to combat online abuse in archaeology. The document is available via The Online Archaeologist and will be available until 31 December 2015.